Ethical Hacking - Ethical Hacking Phases - Fingerprinting Tutorial
A fingerprinting in ethical hacking is use to determine what network protocols, operating system , hardware device , software is being used by target machine.
There are classified into two type of fingerprinting, based on the way of collection information from target system.
- Active Fingerprinting
It involved sending TCP or ICMP Packet to a target machine and analysing the response from target machine.
In active fingerprinting there is a risk of detection is more.
Here, ethical hacker use nmap tools to get response from target machine
- Passive Fingerprinting
It rely on sniffer traces (such as wireshark) of the packets, to determine the operating system of target machine.
It does not involve sending packet to target machine. So chance of detection Is less or no.
It is also be less accurate than active fingerprinting.
There are four important elements that we will look at to determine the operating system
- TTL − What the operating system sets the Time-To-Live on the outbound packet.
- Window Size − What the operating system sets the Window Size at.
- DF − Does the operating system set the Don’t Fragment bit.
- TOS − Does the operating system set the Type of Service, and if so, at what.
Tools Used For Operating System Fingerprinting-
1. p0f – passive OS fingerprinting (http://lcamtuf.coredump.cx/p0f3 )
P0f is a tool that utilizes an array of sophisticated, purely passive traffic fingerprinting mechanisms to identify the players behind any incidental TCP/IP communications (often as little as a single normal SYN) without interfering in any way.
2. Ettercap – passive OS fingerprinting (https://ettercap.github.io/ettercap )
Ettercap is a comprehensive suite for man in the middle attacks. It features sniffing of live connections, content filtering on the fly and many other interesting tricks. It supports active and passive dissection of many protocols and includes many features for network and host analysis.
3. Nmap – active OS fingerprinting (https://nmap.org )
Nmap is a free and open-source utility for network discovery and security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime.
4. XProbe2 – active OS fingerprinting (https://sourceforge.net/projects/xprobe/files/xprobe2 )
Xprobe2 is an active OS Fingerprinting tool with a different approach to operating system fingerprinting. Xprobe2 relies on fuzzy signature matching, probabilistic guesses and multiple simultaneous matches, and a signature database.
Before attack you should know OS of a remote machine. Once target machine OS known, it will be easy to determine the vulnerabilities which can exploit target machine.
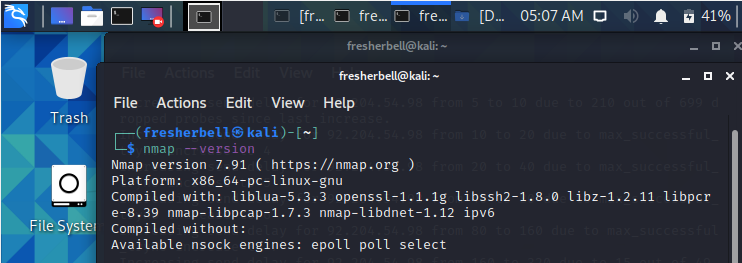
First You Check If nmap is installed on your system using
nmap –version
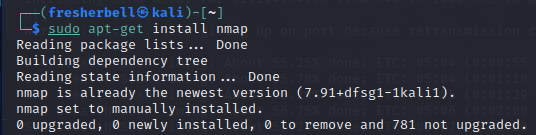
If not,then installed it using-
└─$ sudo apt-get install nmap
Below nmap command is used to know operating system serving the website and the open port within this website.
└─$ sudo nmap -O -v fresherbell.tk
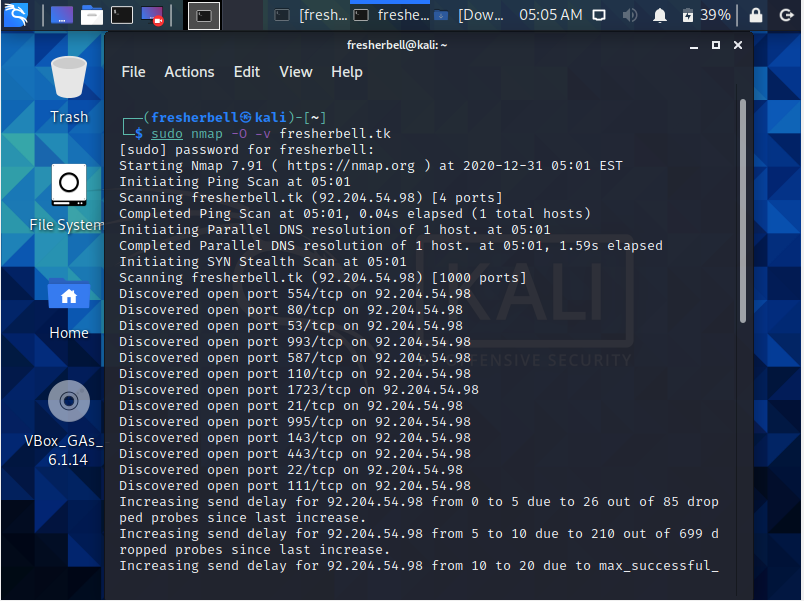
This Command list down all open port
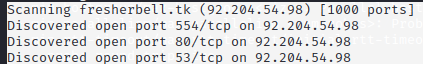
Hacker can use different attack technique through open port.