Ethical Hacking - Ethical Hacking Phases - Common Technique to Gather Information Tutorial
Some of common technique to gather information mostly used over internet are-
- Whois and domain registry
- Finding Ip Address, domain name, track packet (using Ping, nslookup and tracert command)
- Finding Hosting Company
- People Search
- Company information via search engine
- Social network
- Tracking target location
- Whois and domain registry
When we buy a domain, we have to submit some detail which are going to store in domain registry. Domain registry (like godaddy.com, namecheap.com) will supervise a domain.
Using Whois Search https://www.whois.com/ or https://who.is/
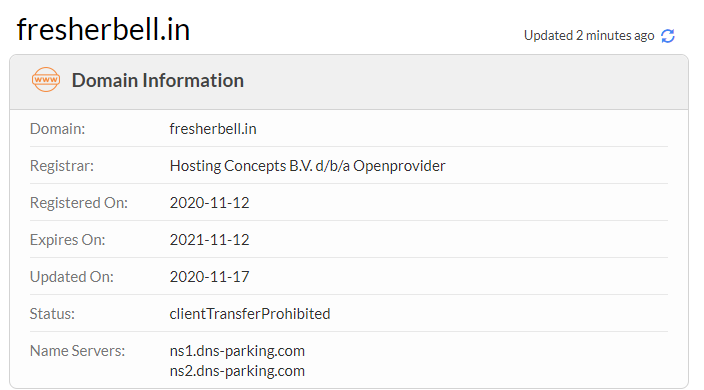
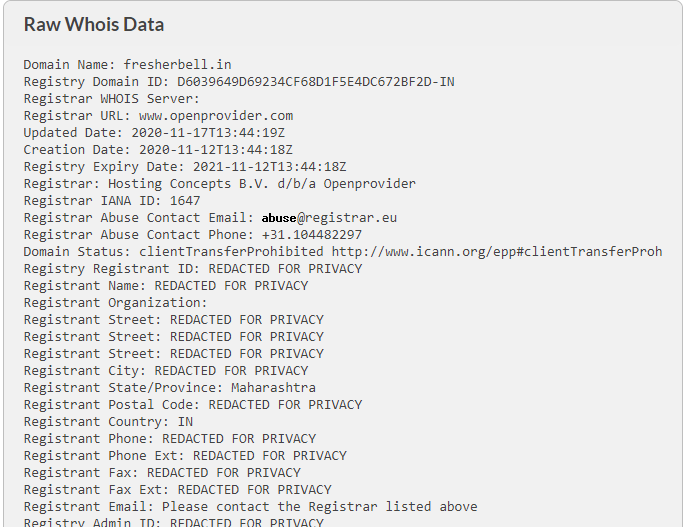
During this phase a hacker can collect information like
- Domain name
- IP address
- Namespace
- Owner Name
- Organisation
- Address
- City
- State
- Postal Code
- Country
- Phone
- Finding Ip Address (using Ping command)
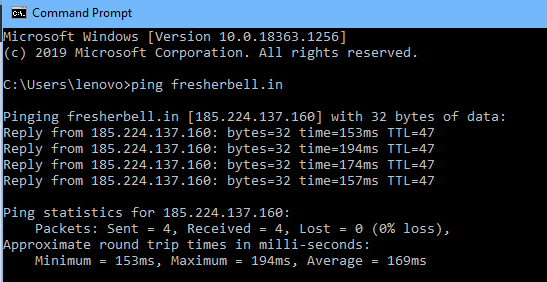
We can use ping command to find out IP address of any domain (e.g google.com) through command prompt.
Ping fresherbell.com
Tracing route of domain name
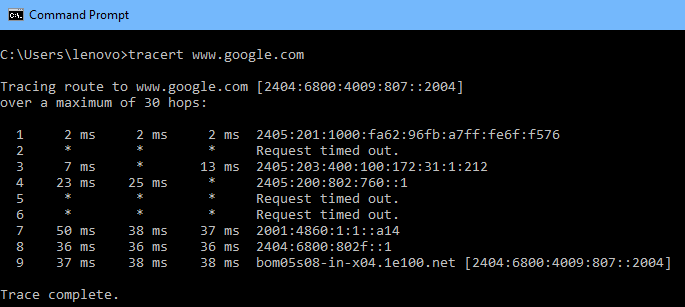
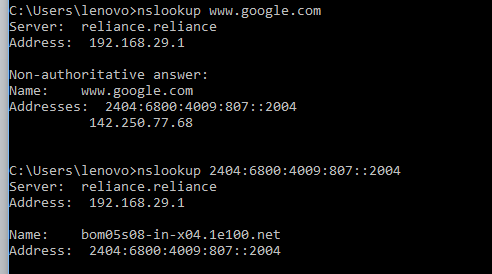
Using nslookup to find IP address
- Finding Hosting Company
Once you have IP address , you can identify geographical location and proxy using below link
- People Search
In this host of a web application provide information about individual at a certain cost.
Here, attacker should know some of the information about target machine such as phone number, email address, name, etc.
Some of this services are:
- Pipl.com https://pipl.com
- Spokeo.com https://www.spokeo.com
- Company information via search engine
Company information can be get from company sites, newspaper, company promotions, social sites, etc.
Using this an attacker can gather as much as information to exploit the target machine.
- Social network
Social network hold very large data of any organisation and its employee.
Using Social Sites, proper test plan can be made of each individual. Which can later be used to execute.
- Tracking target location
It is used by law enforcement agency to track cyber criminal.
It can be tracing through email, or rifling through the header information help track the servers that an email passed through.